Tutorial 1
Let's take a look at the
following picture (click for larger version):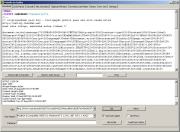
This
is the contents from a link that I've received in a eCard spam mail.
To
get the direct link to malware, we have to deal just with the unescape JavaScript
function.
That's not a big deal, but not all the data supplied
to the unescape
function need to be unescaped,
so, if we are doing it
manually, we would need to take care which part need to be unescaped and
which
part should remain as it is.
Click on Send script to Decoder,
and Run script on
Decoder tab after that brings the following results: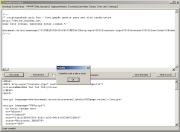
In
the lower box on Decoder tab one can see the results - a VBScript used
to download and run the malicious file.
In
the next example we are dealing with a script that writes directly to a
binary file, no downloading.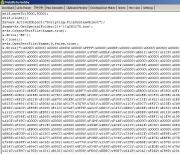
As
the script is written in VBScript, which can't be interpreted by
SpiderMonkey engine, we will use some other Malzilla's functions.
First,
we will copy the data from the script to the box on Misc Decoders tab: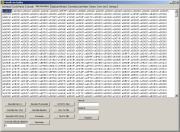
If
you take a look at the first picture from this example, you can see
that the MZ
signature is written to the file in one step, and the rest of the data
in second step.
We will do it in one single step. On previous
picture I have added \u4D5A
at the beginning of the code sequence, which is the ASCII
representation of the letters MZ.
Don't
get fooled by \u
marks in the sequence, this data sequence has nothing to do with
Unicode, as the data is not a text, but just a data that will be
written to a EXE file.
Now, we need to enter \u in Override default delimiter box,
as the next used function would expect the delimiter to be %u, and not \u.
After
clicking on UCS2 To Hex
button, we will have the following situation: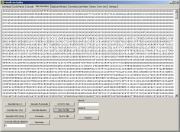
Now,
we will click on Hex To
File and save the result as a binary file on the HDD.
Checking
the resulting file on Virustotal.com reveals the following:
The
next example uses more complicated transformations and math. functions
for decoding the data.
Function eval() is used to
run the result of the decoded data as the result of decoding is also a
script: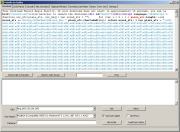
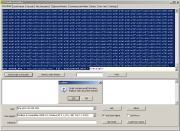
We
will change the eval() function
to document.write() (deprecated in Malzilla 0.9.2, eval() is intercepted automatically),
as we actually want to see the script, not to run it.
The
result of running the script is a VBScript: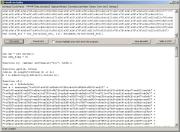
As
you can see, we have a sequence of Unicode codes that needs to be
escaped.
We will copy/paste the sequence to the box on Misc
Decoders tab, and use Decode
UCS2 to see what is hiding there: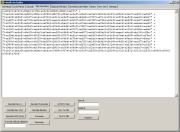
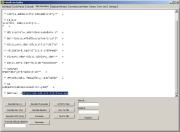
The
result of unescaping is a shellcode, and the download address of the
malware file is visible.
The shellcode looks broken because I
didn't bother to remove quotation and addition marks before clicking
on Decode UCS2.
As
all I want is the link, I do not care about the shellcode.
Next
example is a bit more complicated than previous examples.
It
is using a script known as dF
(after the name of the variable often used in this script, which is
changed to zX
in our sample):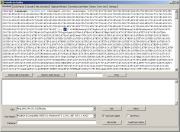
After
clicking on Send Script
To Decoder and running the script, we will have the
following situation: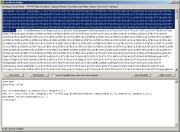
As
you can see, just the first part of the script is decoded (selected
text on the picture, just for the purpose of explaining what is
decoded and what isn't).
Now, we will select the decoded
script (just the script, without <script> tags):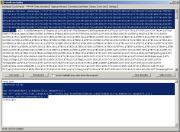
and
copy it over the original part (which is now decoded):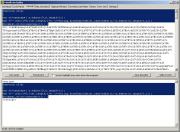
Now,
we will run the whole script again. As can be seen on the next picture,
the result is also a script: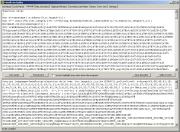
Clear
the upper box, in lower box select the script between the
<script> tags and copy it to the upper box: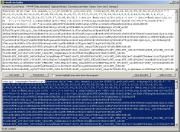
After
running the script again, we have the following results: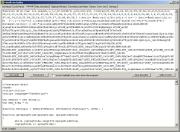
Scrolling
down a bit reveals a sequence of Unicode codes that need to be
unescaped: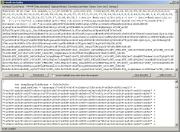
Doing
like in the previous example (copy the data to Misc Decoders tab and
using Decode UCS2 button), we will get the following: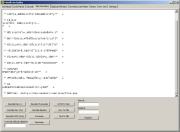
As
it can be seen, it is another shellcode with a plaintext link to the
malicious file.
And one more
example of usage: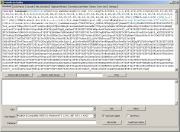
The
transformations used for decoding would take a lot of time if someone
would try to decode the data manually.
In Malzilla you can
just click on Send
Script To Decoder, and Run
script on Decoder tab after that, and you have the
following: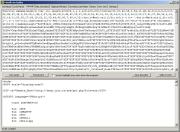
The
link you can see on the picture is a direct link for downloading the
malicious file.
So, that was all for this
time. More examples of Malzilla's usage will follow as soon as I get
some time to write them.