Tutorial 2
Example 1:
Let's take a look at the
following picture (click for larger version):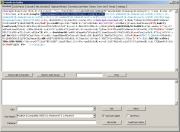
As you can see, this script is using arguments.callee.toString() function which differs between Internet Explorer and Mozilla.
As
almost all the script debugging or decoding tools are based on Mozilla's
Spider Monkey engine, this function is used in malicious scripts
exactly to
make the reversing harder.
In the example script
on the screenshot, the script is done from two parts, so you will need
to copy/paste both parts to Decode tab (see next picture), as Send To
Decoder would send just the first part of the script.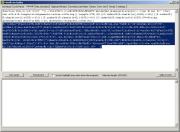
Now, select the function containing arguments.callee.toString() function and take a look at the label Selection length (see next picture).
The length function is oft used because it is a way to check if the eval() function is replaced with e.g. document.write().
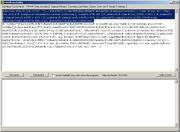
Replace arguments.callee.toString().length function with the value from Selection length: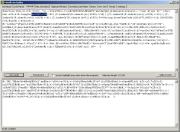
Clicking on Run script
will give us another scrambled output. If you take a look at the 2nd
part of the original script, and take a look at the result, you will
see that both of them are calls to the function H(), which is defined in the first part of the script (the part containing arguments.callee).
Copy the scrambled result and paste it to upper box replacing the 2nd
part of the original script (see next picture, selected part). Clicking
on Run script one more time, and we got what we searched for.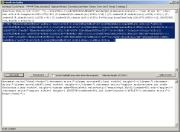
Example 2:
Sometimes
you will still find sites using VBScript to infect visitor's PC. As we
can't decode it automatically, we can try to translate the decoding
routine to other programing language, or sometimes we try the Misc decoders
in Malzilla. In the next example you can see a data sequence which is
obviously a Unicode sequence, but this one can't be decoded with Misc decoders > Decode UCS2 in Malzilla because of missing delimiters between the members in the sequence. 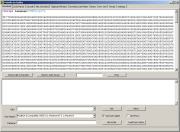
One can either insert the delimiters (usually %u),
or... in Malzilla 0.92 you will find a Pascal interpreter, so you can
write a short routine which will insert missing delimiters: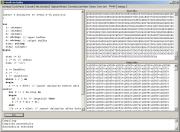
Now you can decode the sequence by using Misc decoders > Decode UCS2.
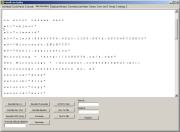
So, that was all for this
time. More examples of Malzilla's usage will follow as soon as I get
some time to write them.