Tutorial 6:
Decoding LuckySploit and a bit about using the disassembler:
What is LuckySploit?Well, it is a very wild animal. We call it LuckySploit after a string we found while analyzing it.
So, what is so special about the LuckySploit?
Maybe you should take a look at this screenshot first:

So, some of the JavaScript code is inside HTML elements.
Well, none of analytic tools handles such things like full DOM implementation.
What now?
There is a way. You can define any HTML DOM as JavaScript object with properties, methods etc. everything that would emulate the HTML DOM we do not have.
Does not look so easy to implement a couple of hundreds of HTML elements by hand.
Thats why we now have that enigmatic Kalimero processor tab in Malzilla.
Copy the entire HTML document into left box and click on Detect. You will get an array on the right side:
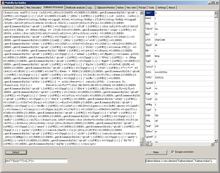
The array is formed according to the regular expression from the box under the detect button.
You may probably need to edit this RegEx in the future if it does not much the exploit form anymore.
Please refer to Malzilla.pdf, found in Docs folder (incl. in Malzilla 1.2.0 and newer versions).
After that click on Make button to get some usable JavaScript code in the left box.
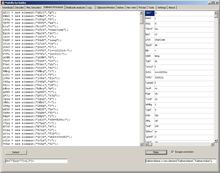
Now we go back to Download tab and click on Send all scripts to Decoder. It will take some time...
After you get the code extracted to Decoder tab, click on Templates button to open templates box.
You should see a template LuckySploit there (included in Malzilla 1.1.0 and newer versions).
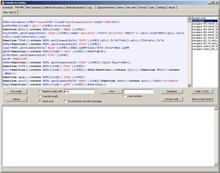
Double-click on the template to import it to decoder.
Please take a look at the beginning of the inserted template. You need to copy the cookie data from the HTTP headers there:
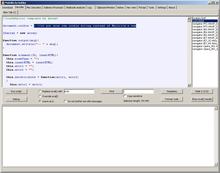
At the end of the template code you need to copy/paste the code you got as result in the Kalimero processor tab:
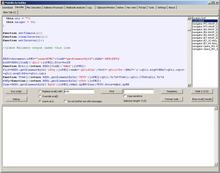
It was about time to click on Run script button.
After long processing ( >30.000 eval calls), we get some results:
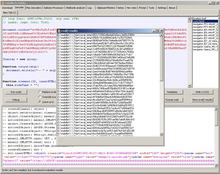
There is some useful info in the results box, generated by the template, and we also get a lot of results of eval() calls.
After inspecting the eval() results, we find that the most of them are useless for further analyze, but one of them reveals some shellcode:
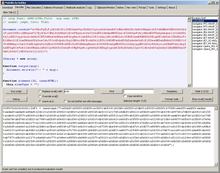
Let's copy that shellcode to the Misc Decoders tab, as we need to do some transformations:
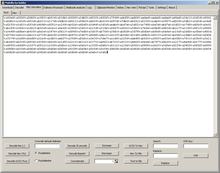
Here, click on UCS2Hex button. Copy the result to Clipboard.
Now, move to Hex view tab, do the right-click on the Hex view box and chose Paste as hex option.
As it can be seen on the right side of the Hex box, there is no download URL visible.
We have either a shellcode that need to be run in emulator, or we have XOR encoded data here.
Let's try Disassemble button.
Scroll to the end of disassembled code to see if the disassembler returned any info:
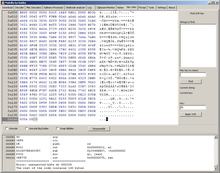
As it can be seen, there is something at the end of the shellcode, and it is not executable.
We need to inspect the code.
At the same beginning of the code, an XOR operation can be found (refer to the lower box on the screenshot):
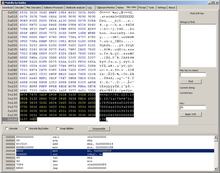
Before the XOR, we have some value moved to al, and the XOR is using that value from al.
Let's try to use that value (3D) to see if it will decode the rest of the shellcode for us.
Type 3D in the Key box and click on Apply XOR button.
As it can be seen from the previous screenshot, the download URL from the shellcode is now visible as plain text.
Thats all folks. See you in the next tutorial.